This is the third blog in our Operational Risk Management series.
In the first article, I explained the incredible KRI system we all have via our five senses. In the second blog, I discussed the application of the Risk and Control Self Assessment (RCSA) in our personal lives using the example of the annual medical check-up. The seven key steps of the RCSA process were set out as part of this example.
In this blog, we will see how the RCSA works in a business context by applying it to a business process. I will use the process of managing employee expense claims, their payment, processing and recording, a process we can all appreciate from one perspective or another.
This example is deliberately at a granular level to illustrate the principles. The same concepts should be used at any level of the organisation using the appropriate level of granularity. This means that the volume of information should be similar for any risk assessment carried out.
Step 1: Business Objectives
The objectives of this process are to:
- Keep employees happy
- Meet contractual requirements (actual if contained in the employment contract and implied if contained in an HR policy)
- Meet external compliance obligations such as Corporations Law and Tax Laws
- Manage expenses
Step 2: Identify critical processes
The critical processes (things we need to successfully complete in order to meet the objectives) are:
- Pay the correct amount

- Pay on time
- Pay the correct bank account
- Have a simple and fair expense policy and expense claim process
- Know what the contractual obligations are
- Meet the contractual obligations. Depending on what they are, items 1,2 & 3 are most likely to meet them
- Know what the external compliance obligations are. We will use typical corporations law and tax law obligations in this example which require proper recording and accounting with adequate supporting documentation
- Post to the correct general ledger account
- Post the correct amount
- Post in the correct period
- Obtain and maintain relevant supporting documentation such as tax invoices
- Prepare and maintain a budget and assess budget vs. actual
- Pay only legitimate expenses
I have listed the critical processes in order of the objectives. However, there is a many to many relationship between objectives and critical processes which means one critical process can meet more than one objective or vice versa.
Step 3: Risks
We can now ask ourselves – what risks exist that could prevent the critical processes from being successfully completed? It is best to address each critical process at a time to ensure all key risks are identified. Again, there is a many to many relationship between critical processes and risks. I have only listed risks relating to the first three critical processes as examples:
- Manual processing error
- System processing error
- Third party bank processing error
- System outage
- Insufficient available funds
Step 4: Controls
For each risk, we then identify the key controls. Below are examples relating to some of the risks noted above.
- Segregation of duties - Review and authorise
- Reconciliation
- Staff resource management
- Back-up systems
- Cash flow planning
Step 5: Assess and analyse the risks
We can now analyse the risks by assessing their likelihood and impact using the pre-determined scales (I am using a simple 1 = Low and 5 = high rating below). We typically find this is best performed by assessing the residual risk first (as this is the level we understand and experience) and then assess inherent risk by reassessing after assuming the recorded controls do not work / exist. I have only assessed one as an example.
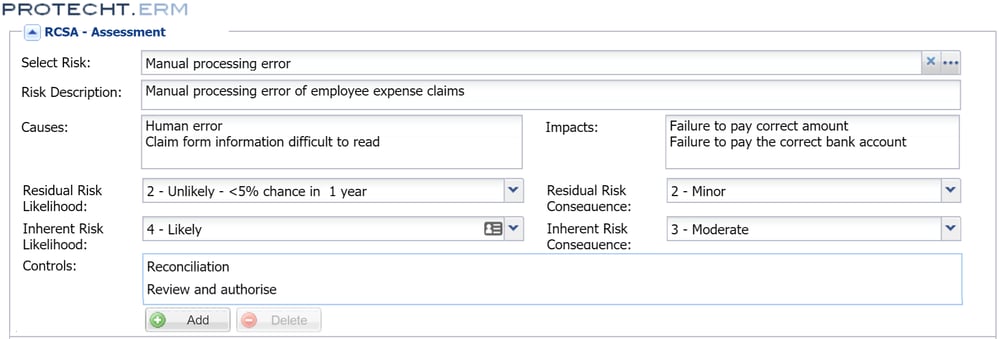
Step 6: Evaluate
Evaluation of the risk is made against the organisations’ risk appetite, commonly using a risk matrix as follows: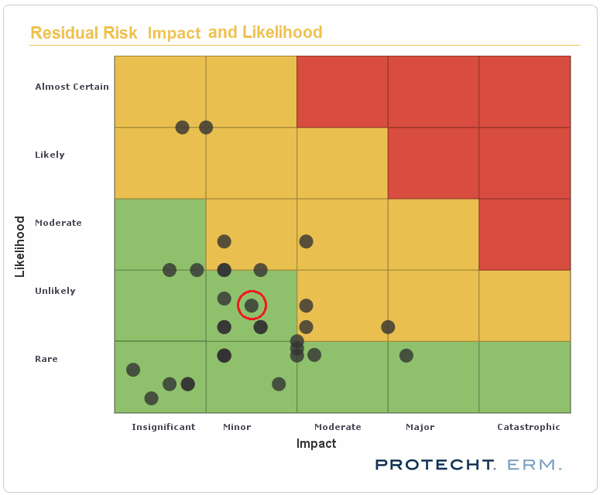
The residual risk for this example is highlighted.
Step 7: Issues and Actions
The evaluation into risk levels then prompts how the risk will be dealt with. Depending on the risk appetite levels, the response may be:
- Accept the risk. This would occur automatically if the risk was within the acceptable level or formally if it was outside of normal acceptance
- Reduce the risk by:
- Increasing controls
- Transferring some of the impact (e.g. Insurance)
- Avoiding by ceasing the process
- Process re-engineering to change the level of inherent risk
- Increasing the risk by:
- Removing or reducing controls because the cost does not outweigh the benefit
- Process re-engineering which increases the level of inherent risk based on increasing reward
The RCSA process when done in this manner has the following advantages:
- It aligns risk management perfectly with business objectives and ultimately strategy
- It helps embed risk management as part of the normal business process
- It overcomes the view that risk management is opposed and works against the achievement of objectives
- It is more engaging with the business as it focusses on the achievement of objectives which is the man focus of business.
Watch our webinar on risk assessment
Learn more about Inherent, Residual and Targeted Risks and how you can leverage each one to add value to your risk management framework. We'll also be sharing some professional hacks for overcoming common issues with using Inherent Risk. Click on the image below to register: 
